- An understanding of the fundamentals of computer networks and security.
- An understanding of the principles of information security management.
- An understanding of the use and benefits of various monitoring and logging tools.
- An understanding of how to create and use security vulnerability and assessment tools.
- An understanding of future network architectures and information security management.
- The opportunity to reflect on and evaluate their personal development.
- The ability to present critical arguments for specific actions or outcomes to a diverse audience.
- Identify and analyse security risks and vulnerabilities in IT network systems and determine appropriate methodologies, tools and techniques to manage and/or solve them.
- Design and critically appraise computer programs and systems to produce solutions that help manage and audit risk and security issues.
- Gather and synthesise information from multiple sources (including internet security alerts & warning sites) to aid in the systematic analysis of security breaches and issues.
- Articulate the legal, social, ethical and professional issues faced by information security professionals.
Ali's E-porfoltio
Network and Information Security Management March 2022
Module 2
Learning outcomes
SUMMARYS and e-Portfolio Activity
Unit 1: Network and Information Security Management: History & Definitions Unit 2: Real World Issues and Implications of Information Security Threats and Vulnerabilities STRIDE and DREAD tools Unit 3: Network Fundamentals Unit 4: Basic Network Investigation Using Standard Tools Unit 5: Network Tools and Components Unit 6: An Evaluation of Commonly Utilised Network Scanning and Vulnerability Testing ToolsWhat have I Learned up to Unit 6
Firstly, A lot of new things such as Starting from the Basic level of understanding of networks and information security including definitions, history, tools techniques, components, and basics + intermediate level structures. Secondly, what are Vulnerabilities, Risks, Breaches, Attacks, threats and how do they affect the technology & how to we can overcome or mitigate these issues technologically. I learned Some information security standards as well. Fundamentals of System logs and forensics. In the last portion, I learned about the future of technology, trends, challenges in information security and how we can overcome these in the future. Further the future of the internet specially IoT, cloud computing and new cutting-edge technologies.
Some whatsApp Meetings
Unit 7: Risks and Standards Unit 8: How to Evaluate and Apply Applicable Security Standards Unit 9: System Logging and Forensics Unit 10: Analysing and Mitigating Security Breaches Unit 11: Future Trends, Technologies and Challenges for the Information Security Industry
- Team 3 My point: Future of the Internet is based on the MobilityFirst
- Group 3 Opening argument
- Executive Summary
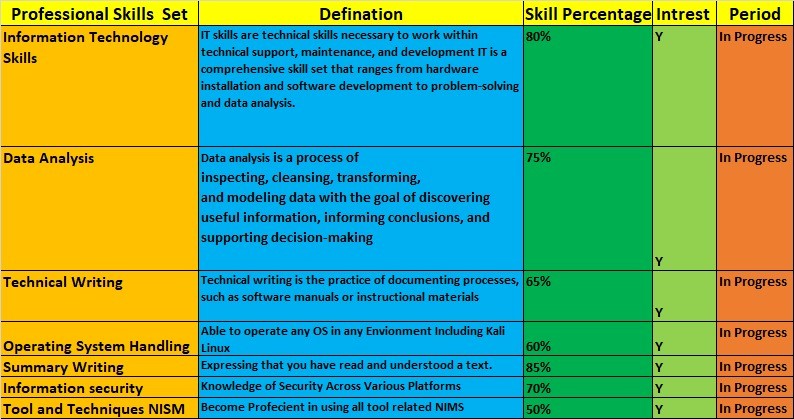
Professional skills
Minutes of meeting
Click here to access G3 Moms Module Artifcats
Collaborative Learning Discussion 1
Medical Mannequin
My reply to Agne Angelides
My reply to Andrijana Klacar
My reply to Jonathan Ashmore
Summary Post
Collaborative Learning Discussion 2
Scanning Exercise and Results
TCP/IP
A design proposal for the penetration testing of a Customer Management System
Collaborative Learning Discussion 3
My reply to Jonathan
My reply to Agne Angelides
My reply to Isioma Vina Okafor-Tolofari
Summary post
Reflections OF 1000 Words "NISM"
Click Here
Collaborative Learning Discussion 1
Medical Mannequin My reply to Agne Angelides My reply to Andrijana Klacar My reply to Jonathan Ashmore Summary Post
Collaborative Learning Discussion 2
Scanning Exercise and Results TCP/IP A design proposal for the penetration testing of a Customer Management System